Wi-Fi Site Surveys, Analysis, Troubleshooting runs on a MacBook (macOS 11+) or any laptop (Windows 7/8/10/11) with a standard 802.11be/ax/ac/n/g/a/b wireless network adapter. Read more about the 802.11be support here.
Who Is on My WiFi?
Until KRACK is fully fixed, everyone needs to pay extra attention to WiFi security, and the cornerstone of any WiFi security approach is strong access control. If you’d like to learn how to see who is on your WiFi, this article is for you.
WiFi security is important
Two researchers from Belgium uncovered a severe flaw in the implementation of Wi-Fi Protected Access II (WPA2) across most wireless devices utilizing this protocol. Referred to as KRACK (Key Reinstallation Attack), this vulnerability exposes sensitive information such as user passwords, payment card details, and private communications to potential attackers.

To address vulnerabilities like KRACK and strengthen wireless security, the Wi-Fi Alliance introduced WPA3, a new and improved security protocol. WPA3 enhances protection by offering stronger encryption and defenses against brute-force attacks. Unlike WPA2, WPA3 includes features such as individualized data encryption, which protects connections even on public Wi-Fi networks.
In addition, the introduction of Wi-Fi 6, Wi-Fi 6E and Wi-Fi 7 brings not only faster speeds and better performance but also integrates WPA3 as a default security measure. The new standards bring improved security and better network performance. Switching to devices that support Wi-Fi 6, Wi-Fi 6E, Wi-Fi 7 and WPA3 can greatly lower security risks and provide more secure connections in our ever-connected world.
How Can I Detect Who Is on My WiFi?
The fastest way way to answer the question, “Who’s on my WiFi?” is to open the NetSpot app on your iPhone. Tap Device Discovery, and within seconds you’ll see a live roster of every device on your Wi-Fi. NetSpot lists the name, IP address, MAC address, vendor, and device class of each client, then pings them for confirmation.
Anything you don’t recognize is a warning sign — tap the entry, copy its MAC address, block it in your router’s admin panel, and change your Wi-Fi password to lock it out for good.
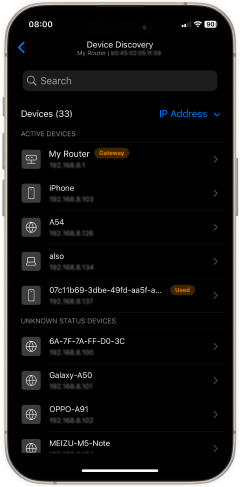
Because Device Discovery refreshes in real time and costs nothing to use, you always have an up-to-the-second view of your network. An expanded profile for each client includes the hostname and, when available, clues about the operating system, making it easy to decide whether that mystery device is yours or a neighbor hitching a ride on your bandwidth.
If you don’t have your iPhone nearby, you can still find every connected client by signing in to your router’s admin interface from any computer or tablet. Virtually all routers keep some sort of a record of past and current connections, usually stating both the IP address of every connected device and its name.
If you notice that an iPhone 15 is connected to your home wireless network even though you don’t own a single Apple device and are sure that neither do your friends and family, it’s possible that the iPhone belongs to someone who has no business being on your network.This might indicate that your network security settings need to be updated.
If your router allows you to disconnect a connected device from the admin interface, don’t hesitate to do so. Just remember to also change your password otherwise the intruder might reconnect the second you go back to minding your own business. It’s also a good idea to periodically review your network settings to ensure that your WiFi remains secure.
How Can I Indirectly Detect Who Is Connected to My WiFi?
There are several clues that can help you indirectly detect that someone is using your WiFi. If you’re lucky, you might even be able to tell who that person is without using any special tools to directly analyze your wireless network.
By using a Wi-Fi analyzer, you can perform partial network intrusion detection and optimize wireless coverage to spot abnormal activities. While NetSpot can’t directly detect intruders, it can indirectly help you identify suspicious devices or usage patterns. Check out a detailed NetSpot review to learn more.
Poor Speeds
If your download and upload speeds are consistently below what they should be, the chances are that someone is on your WiFi, using it to download stuff from the Internet. But don’t be too quick to jump to a conclusion because a single slowdown can be caused by a number of different things, such as a background update process or even a regular maintenance task executed on your router.
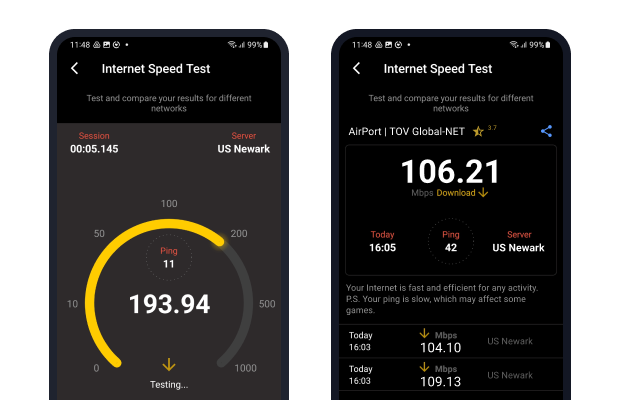
For more accurate results, you can use specialized apps to measure your speed — NetSpot for Android, for example, offers an easy way to test download speeds and monitor network performance changes in real time.
Connection Drops
A sudden connection drop could mean that someone is trying to join your wireless network, most likely using rather brutish means to guess the password, overwhelming your router and causing it to be unresponsive.
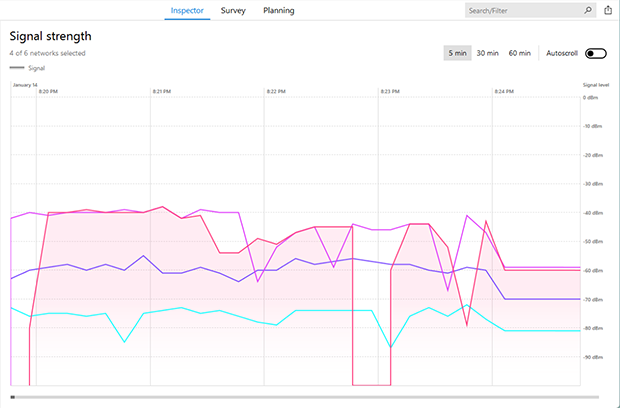
Signal strength graphs available in Wi-Fi analyzers like NetSpot allow real-time monitoring of your network. They visually display signal stability, helping to identify potential issues caused by interference or physical obstacles.
It’s important to note that a drop in signal strength doesn’t always indicate an intrusion. Such drops can result from temporary interference, equipment updates, or environmental changes.
Unknown Connected Devices
If you log into your router’s admin panel and notice unfamiliar devices listed among the connected ones, it might indicate that an unauthorized user is accessing your Wi-Fi network to connect to the Internet.
To determine whether these devices are legitimate, compare their MAC addresses with those of your own devices.Most routers allow you to label known devices or block unknown ones directly from the admin interface. Keep in mind that some of these devices could belong to guests who previously connected to your network. To avoid future confusion, consider setting up a separate guest network for visitors.
Regular Slowdowns
Do your Internet speeds slow down every time your neighbor returns home from work? Then he or she might be using your WiFi, interference from their network could also be a factor. To verify that your suspicion is true, change your WiFi password and do a speed test to see whether your Internet speeds have improved. If they suddenly get worse after a few hours or days, your neighbor might be pretty good when it comes to WiFi hacking.
Why Should I Care Who Is Using My Wi-Fi?
If you don’t depend on fast Internet access and are a generous person by nature, you might be wondering, “Why should I care who’s on my WiFi in the first place?” The answer to this question has everything to do with security and privacy.
Modern wireless networks are typically encrypted to keep unauthorized users out. But when someone connects to your network — whether by stealing your password or being given access — the wireless encryption no longer protects you from them. This means they could snoop on your online activities or even access shared files and devices like printers or smart home systems. While restricting access is possible, it’s much simpler to secure your network from the start.
The Security Risks of Unauthorized Access
Depending on how your computer and other devices are configured, a stranger who joins your WiFi might gain access to the files that you share among computers, printers, and other connected devices. While it’s certainly possible to restrict access to these files, most people lack the required know-how, and it’s almost always easier to stop the intruder before the gates rather than allowing him or her to enter the town and then locking every door individually.
Perhaps the most compelling reason to secure your WiFi is to prevent malware infections and cyberattacks. Malicious software, once on your network, can spread to your devices or even target your router itself. Infected routers can be used for harmful activities, like launching attacks on other networks or stealing sensitive data. Malware such as KRACK and other router exploits highlight the importance of robust security measures.
How to Secure Your WiFi Network
To protect your privacy and devices:
- Choose a strong, unique password and change it periodically.
- Activate WPA3 encryption if your router is compatible.
- Frequently review the list of devices connected to your network for any unfamiliar ones.
- Keep your router firmware updated to patch known vulnerabilities.
Securing your WiFi isn’t just about fast internet — it’s about safeguarding your personal data, devices, and digital life. Take these steps today and enjoy a safer, more reliable network.
Conclusion
Knowing who’s on your Wi-Fi is no longer guesswork. NetSpot’s app for iPhone reveals every connected device in seconds, and your router lets you block strangers just as fast. Together they slam the door on freeloaders before they grab a single byte.
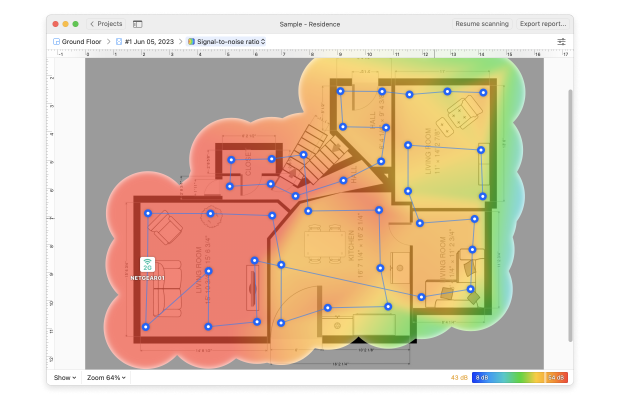
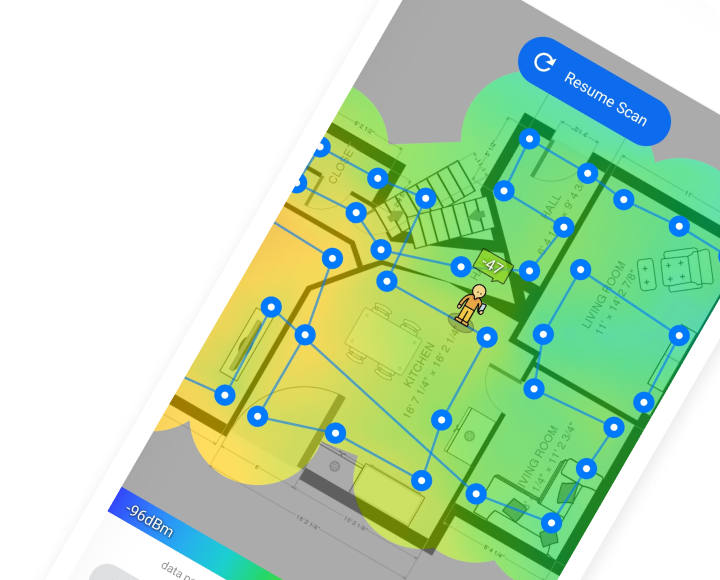
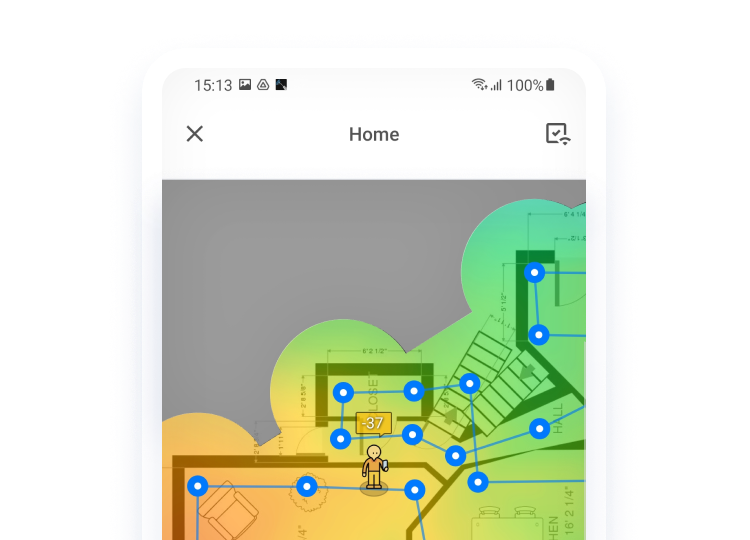
NetSpot does more than name-and-shame unwanted guests. Its survey module can generate an intuitive Wi-Fi heatmap that visualizes signal strength room by room, showing exactly how far from the router someone could stand and still hop on your network. That insight explains why an intruder managed to connect — and where you might need to adjust coverage.
Pair real-time device discovery with heatmap analysis, and you watch your network with precision instead of hope. One app, two powerful views, zero surprises.
What’s more, NetSpot can also give you accurate information about the security of your wireless network, including potential vulnerabilities, as well as the channel on which the network is broadcasted. With the information provided by NetSpot, it’s easy to optimize your WiFi coverage and security, ensuring that strangers can’t steal your bandwidth anymore. Regularly using tools like NetSpot helps keep your WiFi network safe and performing at its best.

Perform an in-depth visual analysis and troubleshoot your WiFi network with comprehensive color-coded heatmaps.
FAQ
NetSpot for iOS shows every device that responds to standard network queries. Truly stealth clients that block pings or spoof MAC addresses may stay invisible, but they are rare on home networks.
A lot of sensitive information is being sent and received over wireless connection: passwords, identity information, payment card credentials, private correspondence, etc. A vulnerability exploit attack on WPA2 — one of the most secure protocols for wireless networks — can intercept and get hold of this important information.
Keeping your security protocol as well as your devices hardware up-to-date is rather important in order to not fall a victim of such an attack.
WPA3 is a newer Wi-Fi security protocol that offers stronger encryption, protection against brute-force attacks, and individualized data encryption on public networks. Upgrading to a WPA3-enabled router helps protect your personal data and reduces the risks associated with vulnerabilities like KRACK.
Most routers log all connected devices, including their IP addresses and device names. You can check your router’s admin interface to spot unfamiliar devices. Many routers also allow you to label known devices or block unknown ones directly, preventing any unauthorized access.
Common indicators include sudden connection drops, unexplained slowdowns, or seeing unknown devices in your router’s interface. In some cases, you may experience sporadic performance issues right when a neighbor returns home, indicating possible Wi-Fi theft or interference.
It is of course up to you, but we wouldn't recommend letting strangers use your WiFi. You might be lucky and someone is just looking for a free way to browse some basic stuff online and disconnects quickly. But what if someone connecting to your network is already infected by malware that spreads over WiFi? To avoid dealing with such an unpleasant situation, we'd recommend keeping your network password-protected and only letting in those people you know personally.
By far the simplest method to find an answer to “Who’s on my WiFi?” question is to check the logs in your router's admin console. Usually you log in by entering your router’s IP address into a web browser search box. Then log in to your router with your credentials, default ones are usually indicated in router's documentation (and yes, it is best if you have changed them!).
Once logged in, find a section dedicated to connected devices and compare their IP or MAC addresses, as well device names to the ones you have. Kick out the ones that look suspicious.
While NetSpot can’t directly detect intruders, it provides Wi-Fi heatmaps and detailed signal strength graphs. This helps you see the coverage area of your router and identify unusual usage patterns or areas where an intruder could gain access. NetSpot also analyzes security settings and channels, making it easier to optimize and secure your Wi-Fi network.
