How to Hack WiFi
Knowing how to hack WiFi networks is the best way to protect yourself against attackers who don't hesitate to exploit WiFi security vulnerabilities. While this knowledge might seem dangerous, it's actually your best defense against becoming the next victim of a cyber attack.
Every day, black hat hackers, phishers, and other cybercriminals are willing to go above and beyond to hack WiFi connections, steal personal information, and profit from unsuspecting users who haven't properly secured their networks.
Why Learn How to Hack Wi-Fi
The more connected we are, the more pressing the question of online security becomes. Sometimes, the best defense is to learn the tactics of your enemy, and that’s certainly the case when it comes to protecting yourself against various online threats.
In this article, we explain how cybercriminals hack WiFi passwords and networks. Knowing how WiFi password hacks are executed will allow you to employ adequate security measures to secure your own network and stay safe online.
The only tool you will need to follow along is NetSpot, a professional Windows, macOS and Android app for wireless site surveys, Wi-Fi analysis, and Wi-Fi troubleshooting. NetSpot is free to download, and it can be installed on any MacBook running , any laptop with , or Android phone, tablet with Android 8.0+.
How to Hack Wi-Fi Passwords
While wireless security standards have evolved significantly since the early days of WiFi, attackers continue to develop sophisticated methods to exploit vulnerabilities. Here are the major types of WiFi hacks that threaten network security today:
- Legacy encryption exploits target networks still using outdated security protocols, particularly WEP (Wired Equivalent Privacy) from 1997, which can be cracked within minutes due to RC4 cipher vulnerabilities. Even WPA networks from 2003 remain vulnerable through TKIP weaknesses.
- WPS brute force attacks exploit the convenience feature known as WiFi Protected Setup, which uses an 8-digit PIN that can be cracked in under 10 hours using tools like Reaver.
- KRACK (Key Reinstallation Attacks) proved that even WPA2 networks could be compromised when researchers demonstrated in 2017 how to manipulate the four-way handshake process to decrypt traffic and inject malicious content. The KRACK vulnerability affected virtually every WiFi-enabled device globally and forced emergency patches across the entire technology industry.
- Evil twin and rogue access points involve the creation of fake WiFi hotspots that mirror legitimate networks and trick users into connecting and exposing all their traffic to interception and credential theft. Many warnings, such as this one from Norton, about this attack have been published over the years, but it still continues to be effective even today.
- Deauthentication and handshake capture attacks force devices to disconnect from their network using specially crafted packets that allow attackers to capture the WPA/WPA2 handshake when devices reconnect, which can then be cracked offline using powerful computing resources. This WiFi password hack technique gained notoriety during the 2014 celebrity photo leaks, where attackers combined deauth attacks with social engineering to gain access to private accounts and home networks.
- Dictionary and Rainbow Table Attacks leverage pre-computed password hashes and massive wordlists to rapidly crack weak passwords. Modern tools like Hashcat can test millions of combinations per second against captured handshakes.
- Man-in-the-Middle (MITM) exploits position attackers between users and their intended destinations once they're on the same network. This enables them to intercept credentials, inject malware, or redirect traffic to phishing sites without detection.
- DNS hijacking and cache poisoning redirect users to malicious websites by compromising router DNS settings or poisoning DNS caches so that hackers can harvest credentials from fake banking or email login pages that appear completely legitimate. A good example of this WiFi hacking technique is the 2019 Sea Turtle campaign, which targeted government and enterprise networks across many countries.
It’s true that modern WPA3 encryption offers enhanced protection against these attacks through improved handshake protocols, forward secrecy, and stronger encryption algorithms, but the sad reality is that many networks remain vulnerable due to outdated equipment, weak passwords, or misconfiguration.
How to Avoid WiFi Hacking
Despite the existence of the WiFi hacking methods described above, there are ways to make your network a significantly harder target and cause most cybercriminals to move on to easier prey:
- Update WiFi and admin passwords: Many successful attacks exploit weak or default credentials that users never bothered to change. Your WiFi password should be at least 12 characters long, combining uppercase and lowercase letters, numbers, and special characters in a completely random pattern that avoids dictionary words, personal information, or predictable sequences. The router's administrative password deserves equal attention since leaving it as "admin" or "password" is like leaving your front door key under the doormat.
- Use the strongest encryption possible: These days, you should only use the latest WPA3 standard because it supports Simultaneous Authentication of Equals (SAE) to protect against offline dictionary attacks, forward secrecy that keeps past sessions secure even if the password is compromised, and enhanced protection for open networks through Opportunistic Wireless Encryption (OWE). If your router doesn’t support it, then you should get a new one.
- Keep firmware and software up-to-date: Manufacturers regularly release patches for newly discovered vulnerabilities that hackers actively exploit in unpatched devices. Enable automatic updates when available, manually check for firmware updates monthly through your router's admin interface, and replace any networking equipment that no longer receives security updates from the manufacturer.
- Monitor connected devices: Access your router's admin panel weekly to review the device list, looking for unfamiliar device names, MAC addresses you don't recognize, or more connections than you expect based on who is on your WiFi. Use tools like NetSpot to scan your network environment and detect potential rogue networks.
- Set up a guest network: Create a separate SSID with its own strong password, enable client isolation to prevent guest devices from communicating with each other, set bandwidth limits to preserve performance for your primary network, and configure time-based access controls that automatically disconnect guests after a set period. The segmentation also makes it easier to manage access and kick people off your WiFi when guests overstay their welcome or when you detect suspicious activity.
- Don't broadcast your router's details unnecessarily: Revealing information about your network configuration gives attackers valuable intelligence for planning their assault. Change the default SSID to something generic that doesn't identify your router's manufacturer or model (avoiding "Linksys" or "NETGEAR_2.4G"). Never include personal information like your name, apartment number, or business name in the network name. Above all else, disable WPS entirely to eliminate PIN-based vulnerabilities.
These security measures create multiple layers of defense that work together to protect your WiFi network from both automated attacks and targeted intrusions.For a comprehensive defense strategy, also check out these 7 ways to stop a WiFi hacker.
Use NetSpot to Find Easy to Hack Wi-Fi Networks
The first thing most hackers do is use a WiFi analyzer tool such as NetSpot to locate WEP-protected networks. Unlike wireless networks that use WPA, WPA2 or WPA3, WEP-protected networks are very easy to hack with nothing but a laptop and the right software.
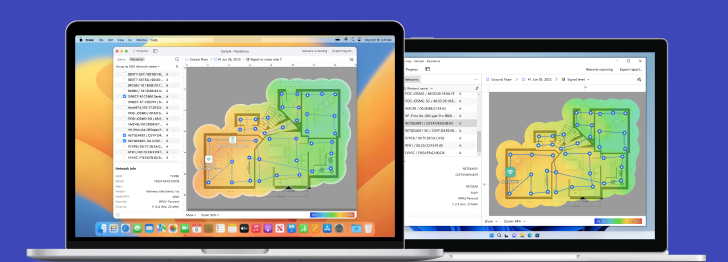
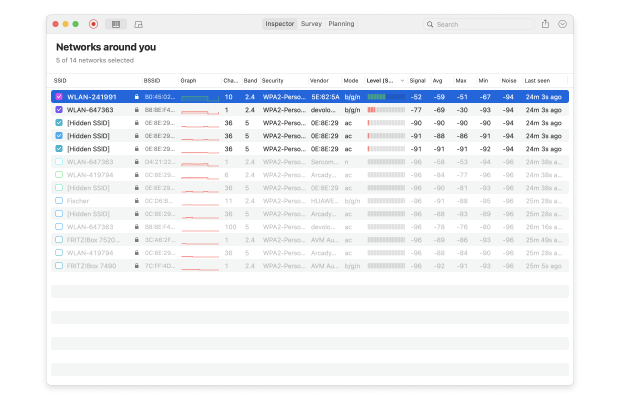
NetSpot has a WiFi analysis mode called Inspector, and you can use this mode to collect every detail about surrounding WiFi networks. NetSpot lets you see the names of the networks around you, their signal level, the channels they broadcast on, and also their security.
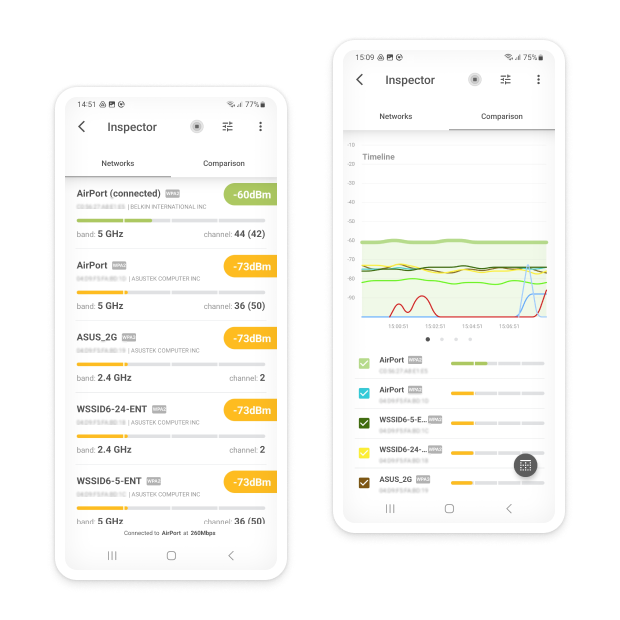
NetSpot for Android offers Wi-Fi Inspector mode allowing you to find and analyze the surrounding Wi-Fi networks on your mobile device.
If you see a network that uses WEP security, you can be sure that anyone can learn how to hack it because learning how to hack a WiFi password isn’t even the difficult part; the difficult part is finding a WiFi network that still relies on WEP security. But with NetSpot, even that’s easy.

How to Secure a Wi-Fi Network Against Hackers
To secure your WiFi network against hackers, you must ensure that it uses a strong wireless security standard and is protected by a secure password.
Launch NetSpot.
Enter Inspector mode.
Locate your WiFi network from the list of available WiFi networks.
Look at the Security column and see if it says “WPA2”.
If it does, your WiFi network meets the basic prerequisite for security.
However, if your WiFi network isn’t secured by WPA2, you need to change your router’s security settings as soon as possible. Because each router is different, the exact steps vary from router to router. Generally, you need to:
Find out your router’s IP address.
Log in to the router’s admin interface.
Look for WiFi security settings.
Select WPA2 as your prefer wireless security standard.
Save the settings and possibly restart your router.
Every time you change your router’s security settings, use NetSpot’s Inspector mode to verify that the settings have really been applied. Besides using WPA2 as your preferred wireless security standard, you also need to choose a strong WiFi password to prevent WiFi password hacks. These are some characteristics of a strong password:
- The password is at least 12 characters long.
- The password uses a combination of letters, numbers, and special characters.
- The password is not commonly used (12345ASFD).
- The password is completely nonsensical.
- The password contains no personal information (birthdate, maiden name, and so on).
- The password is unique and not used anywhere else.
- The password is not written on a piece of paper or saved by the browser.
- The password is not shared with anyone.
Learning how to hack WiFi passwords allows you to better evaluate whether your wireless network is vulnerable to modern cybersecurity threats. With free and easy-to-use WiFi analyzer apps such as NetSpot, you can discover the most obvious weaknesses in your cybersecurity defenses in a matter of seconds.
NetSpot can also optimize the coverage of your wireless network, so you can cover all rooms in your house with a strong WiFi signal and, at the same time, limit the signal only to your house.
FAQ
KRACK ("Key Reinstallation Attacks") is a replay type of network attack that targets WPA2 protocol's flaws. This attack is equally dangerous for all major software platforms, including Microsoft Windows, macOS, iOS, Android, Linux, OpenBSD. The network security protocol that is considered safe can be bypassed, allowing a cybercriminal to intercept the data sent and received over the network.
To get hold of WiFi passwords, hackers use two very different methods. Some hackers take an easy road and exploit lazy WiFi passwords that are easy to crack with a simple dictionary attack. Some hackers will execute advanced attacks with sophisticated ways of obtaining data illegally.
If a network is unprotected and unencrypted, it is easily susceptible to a man-in-the-middle (MITM) attack. An attack is called MITM when a hacker can intercept data because of aforementioned security shortcomings.
There are some things you can do to avoid a KRACK attack:
- Use public WiFi only when you really need it.
- If possible, use wired connection rather than wireless.
- Make sure you are connecting through secure protocols, e.g. HTTPS, STARTTLS, Secure Shell, etc.
- Connect through VPN for an added layer of security.
- Use your own cellular connection instead of connecting to an unprotected wireless network.
- Install updates on your devices, they usually contain patches against the latest security threats.