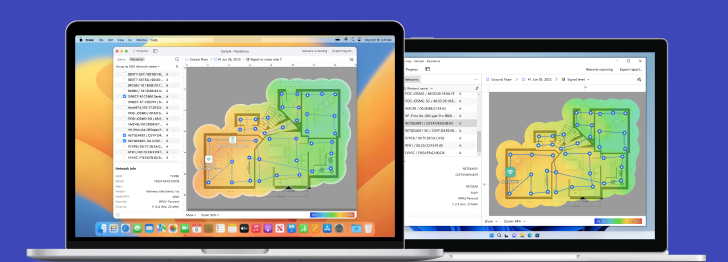
Powerful advanced tool for multiple Wi-Fi networks Surveys, Analysis and Troubleshooting.
Don’t Let Attackers Hack Your WiFi: These Are Our Top WiFi Security Tips
Due to their ubiquitous nature, WiFi networks have become a common attack vector favored by opportunistic hackers looking for fun and profit.
If you’re using WiFi at home to connect to the Internet from your computer or mobile devices, you could become the victim of a WiFi hacker unless you follow our WiFi security tips.
How Can Hackers Hack Wi-Fi Networks?
To hack WiFi passwords, hackers take two vastly different approaches. Some hackers rely on low-skill attacks that exploit weak passwords and naïve users, while others can execute highly technical attacks using cutting-edge exploits and sophisticated, custom-made tools.
Without encryption, the traffic on a WiFi network can be captured and analyzed by everyone within the range of the network. If you’re curious how far can a hacker be from your home router and still have a strong-enough signal to hack your WiFi, you can download NetSpot, an easy-to-use WiFi analysis tool. With NetSpot, you can instantly see whether your WiFi network is sufficiently encrypted to withstand a targeted attack.

Inspect, compare, survey, and analyze WiFi networks with NetSpot.
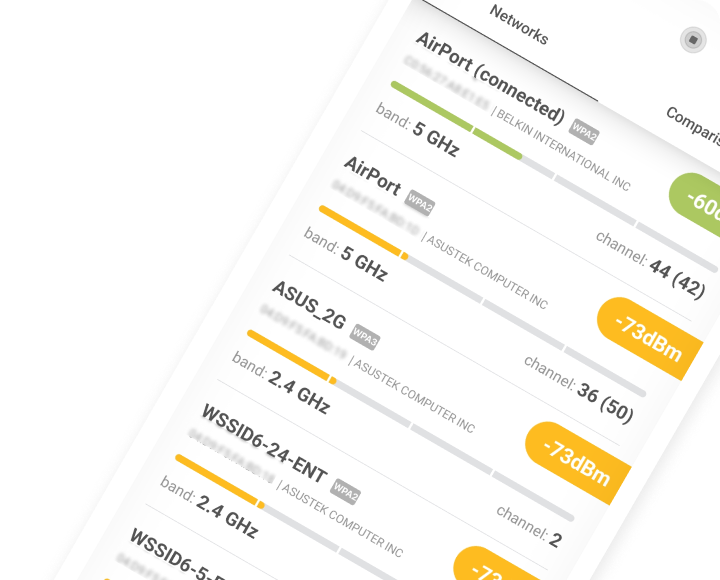
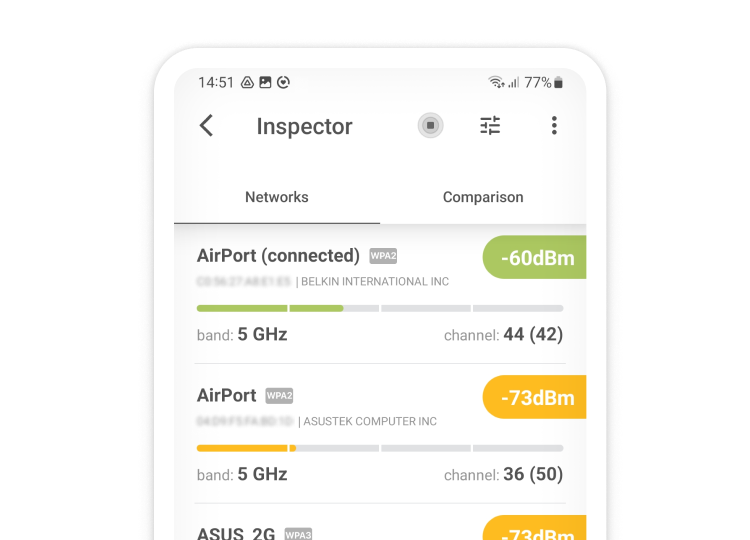
Strong WiFi encryption, such as WPA2 and WPA3, has become an absolute necessity, but even the strongest encryption protocol can be undermined by a weak password. Yes, it can be a drag to remember a ten-digit alphanumerical string of gibberish, but the consequences of a successful WiFi hack can be devastating.
Why Would Someone Learn How to Hack Wi-Fi?
WiFi hackers have various motivations. The best-case scenario is someone hacking your WiFi to steal your bandwidth. The worst-case scenario is someone hacking your WiFi to steal your identity or money. This is something you absolutely don’t want to happen, and our WiFi security tips will help you protect your wireless network against attackers.
Top 8 Ways How to Stop a WiFi Hacker
With so many ways how to hack into WiFi, is it even possible to stay protected against anonymous attackers with a hunger for profit? It is, but it requires some effort on your part. Below are our top 8 recommendations on how you can dramatically improve the security of your WiFi network.
1. Change Your Router Admin Credentials
Do you remember the time when your router arrived, and you went through the initial setup procedure? If so, you probably also remember that you had to input an admin login and password, right? Let us guess: the login name was “admin”, and the password was also “admin”, correct? We thought so.
You see, most routers have the same default admin login name and password, which means that just about anyone could walk right up to your router, connect to it using an ordinary Ethernet cable and mess with the settings. While this is less likely to happen to regular home users, it’s something business owners can’t afford to take lightly. As soon as you can, change the default login credentials for something more secure.
2. Set Up Strong Encryption
Wi-Fi encryption is your main defense against hackers looking for a quick and convenient way how to hack Wi-Fi passwords. Unencrypted wireless communication can be captured, analyzed, and abused. The basic level of WiFi protection is WEP encryption.
While better than nothing, there are many easy-to-follow online tutorials out there that can teach virtually anyone how to hack a WiFi password on a WEP-encrypted network. You should always use at least WPA+TKIP encryption. Ideally, configure your router to use WPA2+AES or WPA3 encryption for a bulletproof security.
3. Verify Connected Devices with NetSpot for iOS
Locking down your network with WPA2 or WPA3 is only half the battle — anyone who slipped in beforehand can stay connected until you boot them out. Grab your iPhone, open NetSpot (a lightning-fast device discovery tool for iPhone) and tap Device Discovery. Within seconds you’ll see a live list of every client, complete with IP, MAC, manufacturer, and device class.
Anything you don’t recognize — an unfamiliar phone, laptop, or smart gadget — deserves the boot: copy its MAC address, drop it into your router’s Access-Control table, and run a fresh scan to confirm the intruder is gone.
4. Keep Your Router Updated
Your router has a complex operating system which isn’t immune to software bugs. A particularly nasty software bug could even allow a hacker from the other side of the world to remotely infiltrate your network and steal your personal information. While most routers these days update automatically, some require you to manually trigger the update process. It’s a good idea to set a reminder on your smartphone to check for available updates at least once a month.
5. Hide Your WiFi Network
The name of your WiFi network is actually called SSID, or Service Set Identifier. You can connect to a WiFi network even if it doesn’t broadcast any SSID, but you’ll need to know the network’s address. As such, hiding your WiFi network by not broadcasting any SSID is an effective way how to prevent the neighborhood kids from using your home WiFi network to hone their hacking skills.
6. Reduce Your WiFi Range
We understand that most people would rather extend the range of their WiFi network than reduce it, but, sometimes, it makes sense to limit the range to a small area. If you’re, for example, living in a small apartment, there’s no reason to broadcast your WiFi across the entire block, giving more people than necessary the opportunity to hack it.
A WiFi analysis tool such as NetSpot can help you determine the current range of your network, and you can then turn down the Transmit Power Control on your router to adjust it.
7. Enable MAC Filtering
Every WiFi-enabled device has a unique identifier called the physical address or Media Access Control (MAC) address. You can set your router to only communicate with certain MAC addresses, preventing everyone else from connecting to your network. Just keep in mind that MAC filtering isn’t bulletproof because it’s easy to change the MAC address on most devices, making them appear as other devices.
8. Avoid Open Public Networks
As convenient as public WiFi networks are, you should be very cautious when connecting to one. Not all public WiFi networks respect the privacy and security of their users, and some public networks may even be set up by hackers who want to lure in unsuspecting victims to steal their passwords and bank accounts. Only connect to verified, trustworthy public networks and always disable automatic WiFi connecting.
Powerful advanced tool for multiple Wi-Fi networks Surveys, Analysis and Troubleshooting.
-
Get NetSpot
macOS 11+, Windows 7/8/10/11
FAQ
To get hold of WiFi passwords, hackers use two very different methods. Some hackers take an easy road and exploit lazy WiFi passwords that are easy to crack with a simple dictionary attack. Some hackers will execute advanced attacks with sophisticated ways of obtaining data illegally.
If a network is unprotected and unencrypted, it is easily susceptible to a man-in-the-middle (MITM) attack. An attack is called MITM when a hacker can intercept data because of aforementioned security shortcomings.
Install NetSpot on your iPhone, open Device Discovery, and you’ll get a live roster of all clients in seconds — perfect for spotting unwanted guests.
Top 8 recommendations on how to improve the security of your WiFi network:
- Change your router username and password.
- Make sure your router has the latest version of encryption protocol.
- Check which devices are connected to your network.
- Update your router firmware.
- Make your WiFi network hidden.
- Reduce your WiFi range.
- Set a strong password for your WiFi network.
- Enable MAC filtering.
WiFi encryption is a must when it comes to keeping your WiFi network safe. The minimal requirement is to have a WPA+TKIP encryption, but it is much better to have the latest encryption protocols implemented. See if you can configure your router to use WPA2+AES encryption, or even WPA3 if it is available.