1999 — 2004 standard. Easy to break and hard to configure. Abandoned.
Wireless Security Protocols : WEP, WPA, WPA2, and WPA3
We'll try to explain the differences among the encryption standards like WEP, WPA, WPA2, and WPA3 so you can see which one will work best for your network environment.
WiFi security algorithms have been through many changes and upgrades since the 1990s to become more secure and effective. Different types of wireless security protocols were developed for home wireless networks protection. The wireless security protocols are WEP, WPA, WPA2 and WPA3, serving the same purpose but being different at the same time.
What is Wireless Security?
Wireless security is about keeping your wireless internet, like Wi-Fi, safe from hackers or unauthorized users. It uses passwords and special encryption methods to make sure only allowed people can access it and that the data sent over it is protected. This helps prevent outsiders from stealing or seeing your information, like your messages or what websites you visit.
How Does Wireless Security Work?
Wireless security works by using passwords and encryption to protect your internet connection. There are different types of encryption, like WPA2 or WPA3, which are just methods to make the data more secure. Such protocols work by implementing security measures like encryption and authentication.
- Encryption: Makes wireless communication unintelligible to anyone but those with the right encryption keys.
- Authentication: Ensures that only those users and devices whose identities have been properly verified can join the network.
When you set up a Wi-Fi network, you create a password. Only people who know this password can join the network. Once connected, encryption scrambles the data sent over the network so that even if someone intercepts it, they can't understand it. Some networks also hide their name or use firewalls to block unwanted traffic, adding extra layers of security.
The downside to the invisible nature of wireless security is that WiFi users often don't pay much attention to it, not knowing which wireless security protocol keeps their networks protected.
Types of Wireless Security Protocols
Wireless security protocols play a crucial role in protecting sensitive information and ensuring privacy when connected to the internet using WiFi. In this section, we are taking a close look at the most commonly used wireless security protocols (WEP, WPA, WPA2, and WPA3) and discussing their features, strengths, and weaknesses.

WEP was developed for wireless networks and approved as a Wi-Fi security standard in September 1999. WEP was supposed to offer the same security level as wired networks, however there are a lot of well-known security issues in WEP, which is also easy to break and hard to configure.
Despite all the work that has been done to improve the WEP system it still is a highly vulnerable solution. Systems that rely on this protocol should be either upgraded or replaced in case security upgrade is not possible. WEP was officially abandoned by the Wi-Fi Alliance in 2004.
For the time the 802.11i wireless security standard was in development, WPA was used as a temporary security enhancement for WEP. One year before WEP was officially abandoned, WPA was formally adopted. Most modern WPA applications use a pre-shared key (PSK), most often referred to as WPA Personal, and the Temporal Key Integrity Protocol or TKIP (/tiːˈkɪp/) for encryption. WPA Enterprise uses an authentication server for keys and certificates generation.
WPA was a significant enhancement over WEP, but as the core components were made so they could be rolled out through firmware upgrades on WEP-enabled devices, they still relied onto exploited elements.
WPA, just like WEP, after being put through proof-of-concept and applied public demonstrations turned out to be pretty vulnerable to intrusion. The attacks that posed the most threat to the protocol were however not the direct ones, but those that were made on Wi-Fi Protected Setup (WPS) — auxiliary system developed to simplify the linking of devices to modern access points.
Powerful advanced tool for multiple Wi-Fi networks Surveys, Analysis and Troubleshooting.
-
Get NetSpot
macOS 11+, Windows 7/8/10/11
The 802.11i wireless security standard based protocol was introduced in 2004. The most important improvement of WPA2 over WPA was the usage of the Advanced Encryption Standard (AES). AES is approved by the U.S. government for encrypting the information classified as top secret, so it must be good enough to protect home networks.
At this time the main vulnerability to a WPA2 system is when the attacker already has access to a secured WiFi network and can gain access to certain keys to perform an attack on other devices on the network. This being said, the security suggestions for the known WPA2 vulnerabilities are mostly significant to the networks of enterprise levels, and not really relevant for small home networks.
Unfortunately, the possibility of attacks via the Wi-Fi Protected Setup (WPS), is still high in the current WPA2-capable access points, which is the issue with WPA too. And even though breaking into a WPA/WPA2 secured network through this hole will take anywhere around 2 to 14 hours it is still a real security issue and WPS should be disabled and it would be good if the access point firmware could be reset to a distribution not supporting WPS to entirely exclude this attack vector.
UPD: WPA3 is the next generation of WiFi security
Protecting Wi-Fi from hackers is one of the most important tasks in cybersecurity. Which is why the arrival of next-generation wireless security protocol WPA3 deserves your attention: Not only is it going to keep Wi-Fi connections safer, but also it will help save you from your own security shortcomings.
Here is what it offers:
Password Protection
Start with how WPA3 will protect you at home. Specifically, it’ll mitigate the damage that might stem from your lazy passwords.
A fundamental weakness of WPA2, the current wireless security protocol that dates back to 2004, is that it lets hackers deploy a so-called offline dictionary attack to guess your password. An attacker can take as many shots as they want at guessing your credentials without being on the same network, cycling through the entire dictionary — and beyond — in relatively short order.
WPA3 will protect against dictionary attacks by implementing a new key exchange protocol. WPA2 used an imperfect four-way handshake between clients and access points to enable encrypted connections; it’s what was behind the notorious KRACK vulnerability that impacted basically every connected device. WPA3 will ditch that in favor of the more secure — and widely vetted — Simultaneous Authentication of Equals handshake.
The other benefit comes in the event that your password gets compromised nonetheless. With this new handshake, WPA3 supports forward secrecy, meaning that any traffic that came across your transom before an outsider gained access will remain encrypted. With WPA2, they can decrypt old traffic as well.
Safer Connections
When WPA2 came along in 2004, the Internet of Things had not yet become anything close to the all-consuming security horror that is its present-day hallmark. No wonder, then, that WPA2 offered no streamlined way to safely onboard these devices to an existing Wi-Fi network. And in fact, the predominant method by which that process happens today — Wi-Fi Protected Setup — has had known vulnerabilities since 2011. WPA3 provides a fix.
Wi-Fi Easy Connect, as the Wi-Fi Alliance calls it, makes it easier to get wireless devices that have no (or limited) screen or input mechanism onto your network. When enabled, you’ll simply use your smartphone to scan a QR code on your router, then scan a QR code on your printer or speaker or other IoT device, and you're set — they're securely connected. With the QR code method, you’re using public key-based encryption to onboard devices that currently largely lack a simple, secure method to do so.
That trend plays out also with Wi-Fi Enhanced Open, which the Wi-Fi Alliance detailed a few weeks before. You've probably heard that you should avoid doing any sensitive browsing or data entry on public Wi-Fi networks. That's because with WPA2, anyone on the same public network as you can observe your activity, and target you with intrusions like man-in-the-middle attacks or traffic sniffing. On WPA3? Not so much.
When you log onto a coffee shop’s WPA3 Wi-Fi with a WPA3 device, your connection will automatically be encrypted without the need for additional credentials. It does so using an established standard called Opportunistic Wireless Encryption.
As with the password protections, WPA3's expanded encryption for public networks also keeps Wi-Fi users safe from a vulnerability they may not realize exists in the first place. In fact, if anything it might make Wi-Fi users feel too secure.
Availability
The Wi-Fi Alliance began the WPA3 certification program in 2018, but it wasn't until 2020 when WPA3 support became mandatory for all devices brandishing the "Wi-Fi CERTIFIED™" logo.
Since then, virtually all manufacturers of WiFi routers have released models that support the latest wireless encryption standard, so there are many options to choose from for those who still rely on older routers that don't support WPA3.
Powerful advanced tool for multiple Wi-Fi networks Surveys, Analysis and Troubleshooting.
-
Get NetSpot
macOS 11+, Windows 7/8/10/11
Which security method will work for your network
Here is the basic rating from best to worst of the modern WiFi security methods available on modern (after 2006) routers:
- WPA3 + AES-CCMP/AES-GCMP
- WPA2 + AES
- WPA + AES
- WPA + TKIP/AES (TKIP is there as a fallback method)
- WPA + TKIP
- WEP
- Open Network (no security at all)
The best way to go is to deactivate Wi-Fi Protected Setup (WPS) and set the router to WPA3 + AES-CCMP/AES-GCMP. As you go down the list, you are getting less security for your network.
Purpose
All wireless encryption standards are supposed to secure wireless Internet networks from unauthorized access. If you leave your router with no security then anyone can steal the bandwidth, perform illegal actions out of your connection and name, monitor your web activity, and easily install malicious apps in your network.
Vulnerability
Older wireless encryption standards leave a lot to be desired in terms of security. The oldest standard to some extent, WEP, is vulnerable to techniques like Wi-Fi deauthentication attacks and ARP re-injection, which make it possible for attackers to compromise WEP-protected networks in minutes.
WPA and WPA2 address the shortcomings of WEP, but, over the years, hackers have discovered several vulnerabilities, like the KRACK ("Key Reinstallation Attack") replay attack, that make networks protected by these standards less than secure.
That's why it's best to use WPA3 whenever possible. Thanks to its Simultaneous Authentication of Equals (SAE) exchange, the standard offers far more secure initial key exchange.
WPA vs. WPA2
WiFi routers support a variety of security protocols to secure wireless networks: WEP, WPA and WPA2. However WPA2 is recommended over its predecessor WPA (Wi-Fi Protected Access).
Probably the only downside of WPA2 is how much processing power it needs to protect your network. This means more powerful hardware is needed to avoid lower network performance. This issue concerns older access points that were implemented before WPA2 and only support WPA2 via a firmware upgrade. Most of the current access points have been supplied with more capable hardware.
Definitely use WPA2 if you can and only use WPA if there is no way your access point will support WPA2. Using WPA is also a possibility when your access point regularly experiences high loads and the network speed suffers from the WPA2 usage. When security is the top priority then rolling back is not an option, instead one should seriously consider getting better access points. WEP has to be used if there is no possibility to use any of the WPA standards.
Performance
It's no coincidence that the weakest encryption standard, WEP, is also the fastest one. That said, you definitely don't want to compromise the security of your WiFi network just to improve your performance because the potential gains are never worth the risk.
If you do care about performance a lot, then you can always purchase a better router, one with enough processing capacity to eliminate slowdowns while keeping you as secure as possible.
Protect Your Wi-Fi Network
While WPA3 offers more protection than WPA2 and therefore provides even more protection than WPA and WEP, the security of your router heavily depends on the password you set. WPA, WPA2, WPA3 let you use passwords of up to 63 characters.
Use as many various characters in your WiFi network password as possible. Hackers are interested in easier targets, if they can't break your password in several minutes, they will most likely move on to look for more vulnerable networks. Summary:
- WPA3 is the latest wireless encryption standard;
- WPA2 is the enhanced version of the original WPA standard;
- WPA only supports TKIP encryption while WPA2 and WPA3 supports AES;
- WPA3 introduces the Simultaneous Authentication of Equals as a new authentication method to protect against attacks on weak passwords;
- Use NetSpot to check your encryption! Once you’ve locked things down with WPA2 or WPA3, fire up NetSpot on your iPhone, tap Device Discovery, and let it scan. In a couple of seconds you’ll see every phone, laptop, and smart gadget that’s actually connected. Any device you don’t recognize is fair game for eviction — copy its MAC address, paste it into your router’s block list, then rerun the scan to confirm it’s gone.

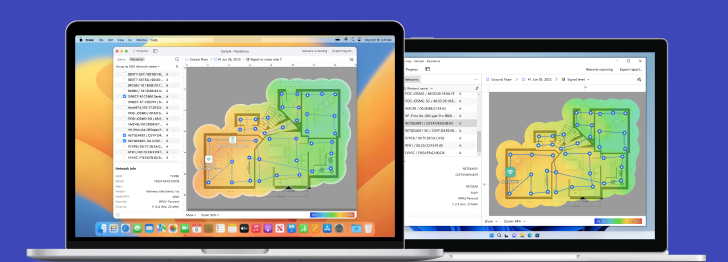
Inspect, compare, survey, and analyze WiFi networks with NetSpot.
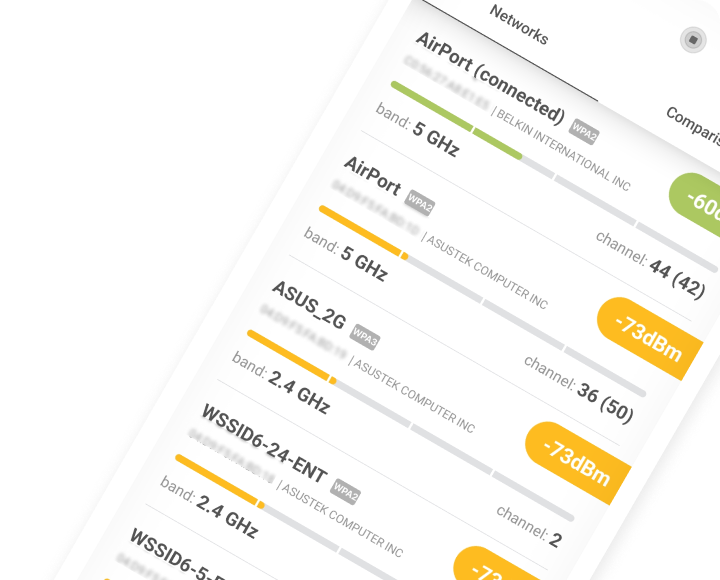
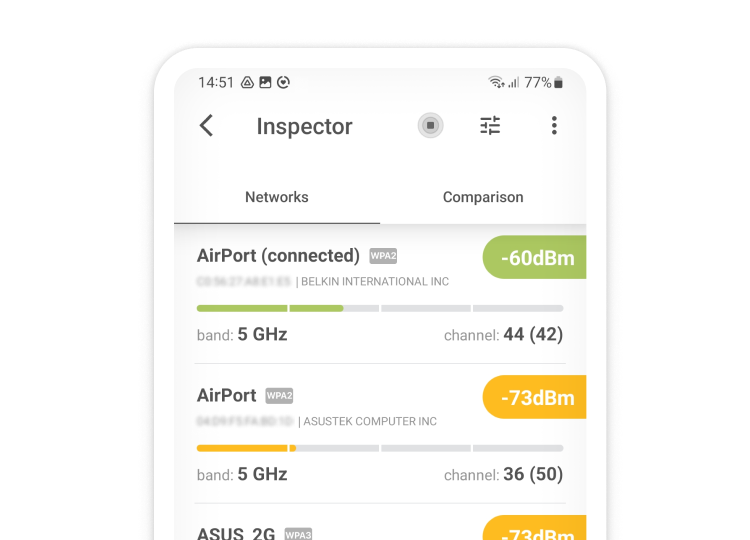
Conclusion
Now that you understand the differences between available wireless security protocols, you should put your newly acquired knowledge to good use by configuring your router to use the newest supported protocol. If your router is so old that it doesn't support even WPA2 — let alone WPA3 — then it's definitely the right time to get a new one otherwise you could experience a costly cybersecurity incident.
Powerful advanced tool for multiple Wi-Fi networks Surveys, Analysis and Troubleshooting.
-
Get NetSpot
macOS 11+, Windows 7/8/10/11
Wireless Security Protocols FAQs
There are WEP, WPA, WPA2, and WPA3 wireless security protocols:
- WEP (Wired Equivalent Privacy) was approved as a Wi-Fi security standard in September 1999. Initially WEP was expected to offer the same security level for wireless networks as wired networks do, however there are a lot of well-known issues in WEP, which are easy to exploit.
- WPA (Wi-Fi Protected Access) was used as a temporary security enhancement for WEP while the 802.11i wireless security standard was in its development stage. One year before WEP was officially dropped, WPA was formally adopted. Even though WPA was a significant enhancement over WEP, its big issue was that the core components were made so they could be rolled out through firmware upgrades on WEP-enabled devices, so it didn't provide enough security from hacker attacks.
- WPA2 (Wi-Fi Protected Access version 2) was introduced in 2004. The most important improvement this 802.11i wireless security standard offered over its predecessor was the implementation of the Advanced Encryption Standard (AES). AES is approved by the U.S. government for encryption of the top secret data, which speaks for itself. The issue with WPA2 is that if an attacker has direct access to a secured network and can gain access to certain keys they can perform an attack on other devices on the network. This issue is considered significant only for enterprise level networks, smaller and home networks are usually not the target.
- WPA3 (Wi-Fi Protected Access version 3) is the latest security protocol with top standards. WPA3 protects against dictionary attacks and uses Simultaneous Authentication of Equals handshake, which protects its network from attacks that could be possible with WPA2 in place. WPA3 is really good on public networks (say in a coffee place), because it automatically encrypts the connection without any need for additional credentials.
Here's the list of modern (after 2006) security methods used on wireless networks, from best to worst:
- WPA3 + AES-CCMP/AES-GCMP
- WPA2 + AES
- WPA + AES
- WPA + TKIP/AES (TKIP as a fallback method)
- WPA + TKIP
- WEP
- Open Network (no security at all)
Security protocols are important, and the later the version the better your network is protected. But it is also crucial to set a solid password for your network. WPA and WPA2 protocols let you set passwords of up to 63 characters. Make your password hard to break by using special characters, lower and uppercase letters and numbers, avoid simple dictionary words.
You should use WPA3 whenever possible, because the encryption technology is far more secure than WPA2.
The best encryption technology currently available for Wi-Fi is called WPA3. If your router doesn't support it, then you should consider upgrading to one that does.
There are several important differences between the three wireless encryption standards. In terms of encryption strength, WEP uses a 40-bit encryption key, WPA uses a 128-bit encryption key, and WPA2 uses a 256-bit encryption key. The standards also support different authentication methods, with newer methods being significantly more secure than older ones.